Hacked, but not cracked: From cyberattack to resilience

Imagine you’re responsible for retail technology operations in one of Europe’s busiest airport environments. Tens of thousands of travelers pass through daily. Millions in daily revenue. Then, at 5:35 AM one morning in January, everything stops.
No sales data. No shift plans. No access to systems. Just a ransom note.
That’s exactly what happened to Travel Retail Norway (TRN), a company operating duty-free and travel value stores across four Norwegian airports, including the country’s largest retail space at Oslo Airport. If you’re a CIO, CISO, or IT operations lead, this is a situation you hope you’ll never have to live through. But it’s one worth learning from. Because what followed wasn’t panic, but swift, calm, and coordinated action.
What happens when your systems go dark?
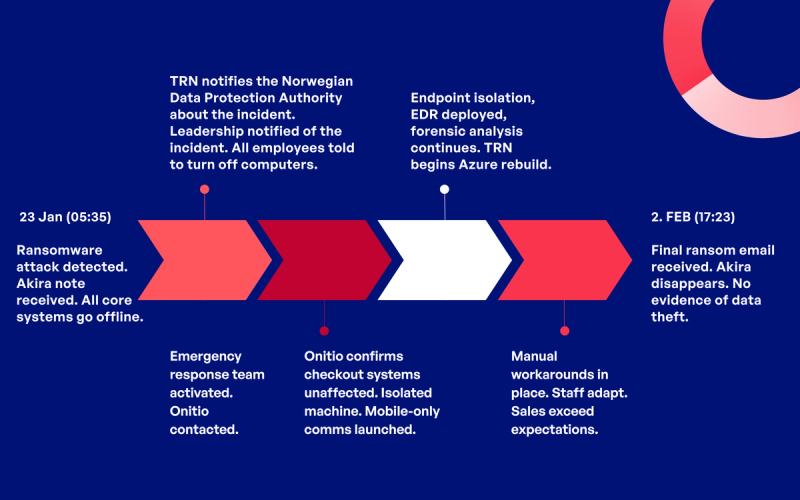
In the early hours on the 23rd of January, Travel Retail Norway was hit by a ransomware attack that brought its entire digital infrastructure to a standstill.
Systems went dark. Schedules vanished. Self-checkouts failed. Laptops were useless, and 1,000 employees lost access to the tools they relied on daily.
The attackers, a group calling themselves Akira, left a simple message.
“Hi friends… Your internal infrastructure is fully or partially dead. All backups removed.”
The fallout was immediate, affecting nearly every digital touchpoint.
- All digital applications failed (except manual tills and payment terminals).
- Self-checkouts were offline.
- Staff scheduling disappeared overnight.
- Access to documentation, sales data, and internal communication tools was lost.
- Laptops were unusable. Only mobile phones remained functional.
For most organizations, this would result in widespread chaos and panic. For TRN, it marked a turning point.
Crisis response: Leading without laptops
Despite the scale of the attack, TRN kept operating, and customer experience, remarkably, improved. They established an emergency response protocol within hours. Key actions included:
- Twice-daily IT and leadership coordination meetings.
- Daily video updates to store managers.
- Weekly livestreams from the CEO to maintain transparency.
- Company-wide communication via mobile-first platforms.
- Task forces formed for frontline coordination.
A new internal motto emerged: “Information overload = success.” In the absence of systems, consistent communication became the glue that held the business together. Leaders delegated, staff adapted, and customers remained served.
Onitio’s role: Containing risk, enabling recovery
TRN contacted Onitio within hours of detecting the attack. Our team was brought in to help assess the situation, particularly the integrity of the checkout system, the backbone of airport retail operations.
In the early phase of the cyberattack, when the situation was marked by uncertainty and chaos, it was reassuring to have Onitio as a trusted partner. They did everything they could to ensure that sales in our stores could continue as normal. Onitio demonstrated great flexibility and decisiveness and were a key source of reassurance in a very demanding time.
In those critical early hours, we worked to map the scope of the breach. Using our access to the retail environment, we quickly gathered data and provided assurance that the checkout system, running on a separate network, had not been compromised.
Our threat intelligence team searched for known indicators of compromise linked to the Akira group and found traces of the attack on several administrative endpoints, confirming that the attackers had targeted back-office systems.
We isolated a compromised account and analyzed network traffic against known malicious infrastructure. Meanwhile, we reported our findings to TRN’s crisis team to support their decision-making and incident response.
Over the following days, Onitio helped implement technical controls to prevent reinfection. We:
- Deployed WithSecure Endpoint Detection and Response (EDR), strengthening endpoint protection and increasing visibility.
- Decoupled the checkout environment from the compromised domain.
- Increased monitoring across sales-critical systems.
- Rerouted network traffic and performed deep log analysis.
Between 23 January and 7 February, Onitio provided nearly 150 hours of cyber forensics, security architecture, and network engineering support, focused on stabilizing operations and restoring control. These actions enabled TRN to safely resume sales, click-and-collect, and customer service with minimal risk.
Rebuilding from scratch, and rethinking everything
Rather than attempting to restore broken infrastructure, TRN made a deliberate choice to rebuild its IT environment from the ground up in Microsoft Azure, a move that accelerated its Azure cloud migration strategy.
This decision offered three major advantages:
- A clean break from legacy vulnerabilities.
- An opportunity to simplify and reduce digital clutter.
- Greater flexibility and resilience going forward.
Manual workarounds were implemented quickly. Pricing and transactions were managed by hand. Shift coordination moved to mobile messaging. And while the systems were being rebuilt, operations continued, and sales outperformed expectations.
Culture over technology
What emerged during the crisis was not just operational ingenuity, but cultural resilience.
- Managers returned to the shop floor and worked side by side with staff.
- Teams across locations began sharing improvised solutions.
- Creativity thrived in the absence of routine.
Freed from screens and schedules, leaders became more visible and responsive. Decision-making became local, direct, and fast. Trust replaced control. Culture, not code, carried business forward.
What retailers can learn from TRN
1. Not every system needs to come back.
The attack prompted a reassessment of digital priorities. Redundant applications were left behind. Fewer systems meant less complexity—and fewer vulnerabilities.
2. Communication is a critical function of IT.
Crisis communication isn’t just a PR task. It’s an operational discipline. Clear, consistent updates replaced dashboards and provided stability.
3. The cloud is not an upgrade. It’s insurance.
Rebuilding in Azure allowed TRN to modernize its stack while insulating against future incidents.
4. Security is now a leadership issue.
The breach elevated cybersecurity to the executive agenda. TRN responded with transparency, speed, and a long-term view.
5. Resilience comes from people.
TRN’s systems might’ve failed, but its people didn’t. Culture, creativity, and calm leadership were the most effective tools in recovery.
What comes after recovery?
On 2nd of February, 10 days after the attack, one final ransom note arrived. Then, silence. No further threats. No confirmed data leaks. No further contact. Akira disappeared.
TRN, however, pressed forward.
But their recovery was not just a return to baseline. It was a strategic reset. Not all systems were reactivated. Not all routines reinstated. The crisis became a filter: what adds value stays; what doesn’t is left behind.
Summary
Cyberattacks on retailers are rising, both in frequency and impact. As businesses digitize from checkout to supply chain, the risk landscape expands, often faster than defenses can keep up.
In 2023 alone, ransomware attacks increased by 68% globally, according to IBM’s X-Force Threat Intelligence Index. The retail sector ranked among the top five most targeted industries, with attackers exploiting high transaction volumes and distributed systems.
Meanwhile, Sophos reports that retail organizations saw the highest average ransom demand of any industry, with recovery costs exceeding $1.5 million USD on average per incident.
TRN’s story is a reminder that resilience isn't built on backups alone. It’s shaped by clarity, leadership, and culture under pressure. If your systems went dark tomorrow, would your teams know how to lead?
TRN did. They didn’t just survive a cyberattack, they improved because of it. And in many ways, reinventing what it means to run secure, resilient retail operations at scale.
Hacked, yes. Cracked? Not even close.
What happens when support fails?

Dig deeper into the hidden risks of poor customer support, from lost revenue and operational disruption to customer churn and long-term reputational damage. This article unpacks real-world examples and offers a practical framework for building a resilient, future-ready support model that protects business continuity.